|
1 | 1 | # Security Features |
2 | 2 |
|
3 | | -{% hint style="info" %} |
4 | | -### Prerequisite |
| 3 | +## Introduction |
5 | 4 |
|
6 | | -Install any one of the following integrations for scanning vulnerabilities: |
7 | | -* [Clair](../user-guide/integrations/clair.md) |
8 | | -* Trivy |
9 | | -{% endhint %} |
| 5 | +Devtron provides [DevSecOps](https://devtron.ai/product/devsecops) capabilities across your software development life cycle for both: the default CI/CD solution by Devtron as well as your existing CI/CD Tools. |
| 6 | + |
| 7 | +One of the key components of DevSecOps is the detection of security risks. Currently, Devtron supports the following types of scanning: |
| 8 | + |
| 9 | +* Image Scan |
| 10 | +* Code Scan |
| 11 | +* Kubernetes Manifest Scan |
| 12 | + |
| 13 | +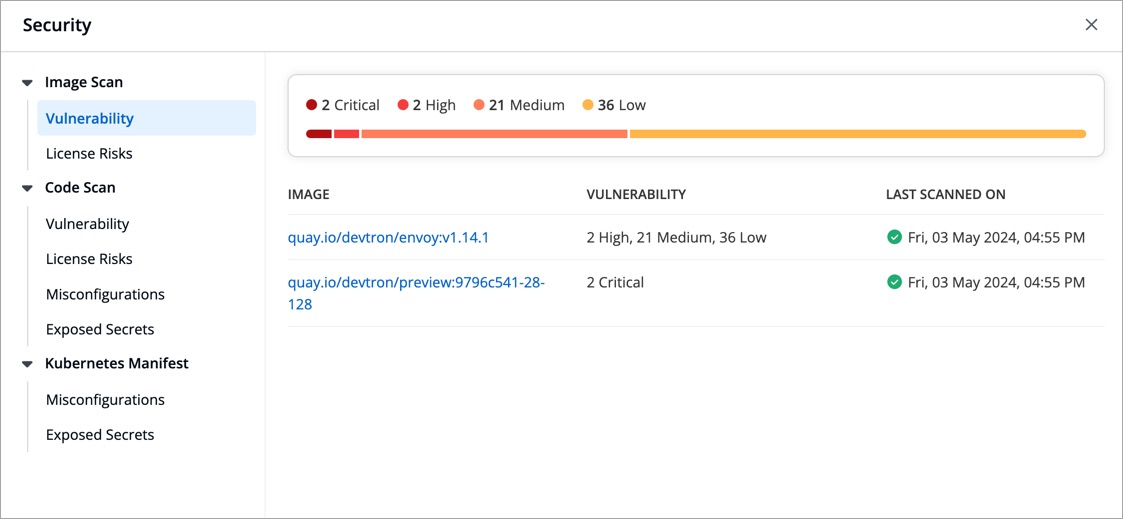 |
| 14 | + |
| 15 | +You can integrate a scanning tool of your choice. By default, Devtron integrates with Trivy using which you can scan for the following issues: |
| 16 | + |
| 17 | +* Vulnerability |
| 18 | +* License Risks |
| 19 | +* Misconfigurations |
| 20 | +* Exposed Secrets |
| 21 | + |
| 22 | +--- |
| 23 | + |
| 24 | +## Where to Initiate the Scan |
| 25 | + |
| 26 | +### Before Building Artifact |
| 27 | + |
| 28 | +When you commit the code, it's essential to scan it before building a [container image](../reference/glossary.md#image). By scanning early, you can catch and fix problems before they become expensive or time-consuming to remediate later. |
| 29 | + |
| 30 | + |
| 31 | + |
| 32 | +1. In your application, go to **App Configuration** → **Workflow Editor**. |
| 33 | + |
| 34 | +2. Click the CI pipeline of your preferred workflow. |
| 35 | + |
| 36 | +3. Go to the **Pre-build stage** (tab). |
| 37 | + |
| 38 | +4. Click **+ Add Task**. |
| 39 | + |
| 40 | +5. Choose **Vulnerability_Scanner v1.0.0** plugin from the list. |
| 41 | + |
| 42 | +6. Click **Update Pipeline**. |
| 43 | + |
| 44 | +Based on the results of the scanner, you can also decide whether your CI should proceed further or not. This is possible through **Pass/Failure Condition** setting in the plugin. In the below example, we are allowing image build only if the no. of high vulnerability is zero. |
| 45 | + |
| 46 | + |
| 47 | + |
| 48 | +Results of Pre-CI scan will be visible under `Code Scan` in the **App Details** page as shown below. |
| 49 | + |
| 50 | + |
| 51 | + |
| 52 | +### After Building Container Image |
| 53 | + |
| 54 | +Once a container image is ready, you can scan its base image libraries, stale files, compromised licenses, and many more. |
| 55 | + |
| 56 | +There are 2 options available: |
| 57 | +* Image scan in the Build stage (refer [Security Scans](./security-features/security-scans.md)) |
| 58 | +* Comprehensive scan in Post-Build stage |
| 59 | + |
| 60 | +This section contains the steps for comprehensive scan. |
| 61 | + |
| 62 | + |
| 63 | + |
| 64 | +1. Go to the **Post-build stage** (tab) of your CI pipeline. |
| 65 | + |
| 66 | +2. Click **+ Add Task** and choose **Vulnerability_Scanner v1.0.0**. |
10 | 67 |
|
11 | | -Devtron's security feature consists of two primary components: |
| 68 | +3. Click **Update Pipeline**. |
12 | 69 |
|
13 | | -1. [Security Scans](./security-features/security-scans.md) - This allows you to identify and address potential security risks effectively. By leveraging this feature, you can ensure that your containerized applications are safeguarded against known vulnerabilities. |
| 70 | +Results of Post-CI scan will be visible under `Image Scan` in the **App Details** page as shown below. |
14 | 71 |
|
15 | | -2. [Security Policies](./security-features/security-policies.md) - This allows you to define policies to block or allow the deployment of container images depending on the vulnerabilities detected. |
| 72 | + |
| 73 | + |
| 74 | +### Before Triggering Deployment |
| 75 | + |
| 76 | +There can be a loophole where the original image built in the CI stage gets compromised later (say, in publicly accessible repository). Therefore, you can scan the image and catch issues before deploying it. On top of that, you can also scan manifests to detect misconfigurations and exposed secrets. |
| 77 | + |
| 78 | + |
| 79 | + |
| 80 | +1. Go to the **Pre-Deployment stage** (tab) of your CD pipeline. |
| 81 | + |
| 82 | +2. Click **+ Add Task** and choose **Vulnerability_Scanner v1.0.0**. |
| 83 | + |
| 84 | +3. Click **Update Pipeline**. |
| 85 | + |
| 86 | +Results of Pre-CD scan will be visible under `Image Scan` and `Kubernetes Manifest` in the **App Details** page as shown below. |
| 87 | + |
| 88 | + |
| 89 | + |
| 90 | +### During Helm App Deployment |
| 91 | + |
| 92 | +When you [deploy a helm chart](../user-guide/deploy-chart/deployment-of-charts.md), Devtron will scan the image associated with that helm chart and also the manifests, but unlike Devtron Apps, there is no code scan involved. |
| 93 | + |
| 94 | +Results of helm app scan will be visible under `Image Scan` and `Kubernetes Manifest` in the **App Details** page as shown below. |
| 95 | + |
| 96 | + |
| 97 | + |
| 98 | +### Extras |
| 99 | + |
| 100 | +You can also check for vulnerabilities within a specific workload such as job, pod, deployment, etc. There are two ways to perform it: |
| 101 | + |
| 102 | +#### From App Details |
| 103 | + |
| 104 | +* Go to **App Details** (Devtron App/Helm App) → **Workloads** (under `K8 Resources` tab). |
| 105 | +* Click a workload, e.g., Pod. |
| 106 | +* On the right-hand side, click the kebab menu (3 vertical dots). |
| 107 | +* Click **Check Vulnerabilities**. |
| 108 | + |
| 109 | +  |
| 110 | + |
| 111 | +#### From Resource Browser |
| 112 | + |
| 113 | +* Go to Resource Browser. |
| 114 | +* Select a cluster. |
| 115 | +* Click a workload within the **Workloads** dropdown. |
| 116 | +* Access the **Check Vulnerabilities** option from the kebab menu present to your selected workload. |
| 117 | + |
| 118 | +  |
| 119 | + |
| 120 | +--- |
| 121 | + |
| 122 | +## Scans and Policies |
16 | 123 |
|
17 | 124 | {% hint style="warning" %} |
18 | 125 | ### Who Can Perform This Action? |
19 | 126 | Users need to have super-admin permission to enable vulnerability scanning and to define security policies in Devtron. |
20 | | -{% endhint %} |
| 127 | +{% endhint %} |
| 128 | + |
| 129 | +Devtron's Security feature has two primary sections: |
| 130 | + |
| 131 | +1. [**Security Scans**](./security-features/security-scans.md) - You can view the vulnerabilities detected across your applications. |
| 132 | + |
| 133 | +2. [**Security Policies**](./security-features/security-policies.md) - This allows you to define guardrails to block or allow the deployment of container images depending on the vulnerabilities detected. |
| 134 | + |
0 commit comments