-
-
Notifications
You must be signed in to change notification settings - Fork 1.5k
[Postfix] Prevent unwanted unauth relaying to other mailservers #6704
New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
Closed
Conversation
This file contains hidden or bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
[Nginx] move conf.d include to end of nginx.conf
…ges (mailcow#6273) * clamd: update to 1.4.2 + build from source instead using alpine packages * clamd: remove exposed ports from buildfile * clamd: cleanup dockerfile
Update 2025-01a
Update 2025-02
Update 2025-02
Update 2025-03
Update 2025-03a
Update 2025-03b
Update 2025-05
Update 2025-05_2
Update 2025-07
In case of unwanted spamfloods your mailcow will relay incoming mails from other mailservers because of a wrong rcpt_to or from: header. I this case you have can secue your mailcow by adding those 2 restrictions, one for external relays and also for the internal usecase, when you may accidently use the wrong relay adress with your auth. In my case I learned that this will deny round about 20k spammails from outside, who tried to use my mailcow as "openrelay" because they used a wrong from/rcpt_to address and my mailcow thought..ok I will relay it back to the "primary" spam destination....
1 similar comment
|
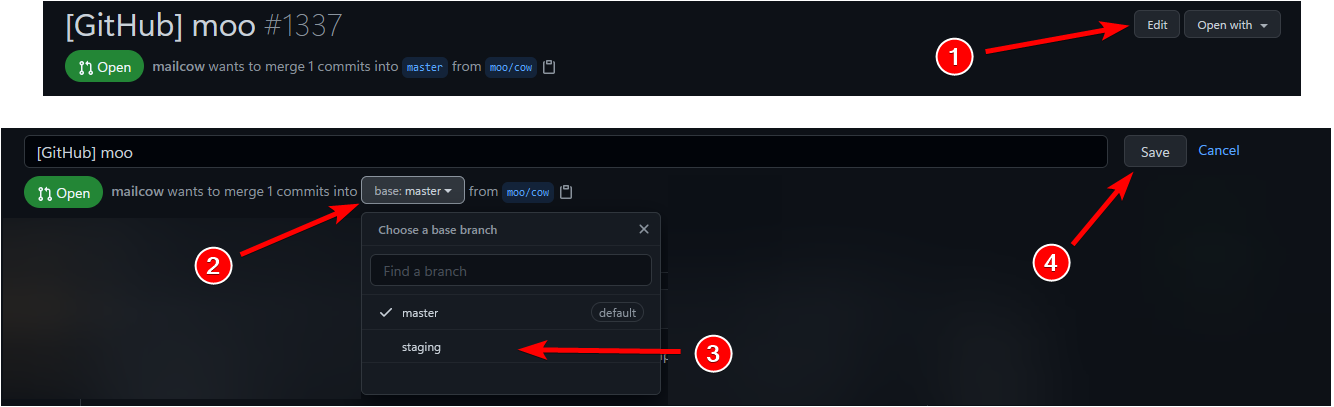
Violating Contrib Rule 3, please reopen based on staging |
|
Let's try this -> #6707 |
Sign up for free
to join this conversation on GitHub.
Already have an account?
Sign in to comment
Labels
not matching contrib guidelines
Whenever a issue/pr is not matching the Guidelines this tag will assigned
Add this suggestion to a batch that can be applied as a single commit.
This suggestion is invalid because no changes were made to the code.
Suggestions cannot be applied while the pull request is closed.
Suggestions cannot be applied while viewing a subset of changes.
Only one suggestion per line can be applied in a batch.
Add this suggestion to a batch that can be applied as a single commit.
Applying suggestions on deleted lines is not supported.
You must change the existing code in this line in order to create a valid suggestion.
Outdated suggestions cannot be applied.
This suggestion has been applied or marked resolved.
Suggestions cannot be applied from pending reviews.
Suggestions cannot be applied on multi-line comments.
Suggestions cannot be applied while the pull request is queued to merge.
Suggestion cannot be applied right now. Please check back later.
In case of unwanted spamfloods your mailcow will relay incoming mails from other mailservers because of a wrong rcpt_to or from: header. I this case you have can secue your mailcow by adding those 2 restrictions, one for external relays and also for the internal usecase, when you may accidently use the wrong relay adress with your auth.
In my case I learned that this will deny round about 20k spammails from outside, who tried to use my mailcow as "openrelay" because they used a wrong from/rcpt_to address and my mailcow thought..ok I will relay it back to the "primary" spam destination....
Contribution Guidelines
What does this PR include?
Short Description
Add 2 more settings to the smtpd_relay_restrictions key to make sure that no other auth or unwanted unauth relaying will happen under a wrong name/permission.
Affected Containers
Did you run tests?
Yes
What did you tested?
I tested from internal/external by script to try to relay to external mailserver an undelivered mail -> denied (expected)
-> Sender address rejected: User unknown in virtual mailbox table;
What were the final results? (Awaited, got)
The default mailcow installaiton is now not anylonger possible to relay a mail from external to another external mailserver and so it's not an openrelay anymore. With the default config you do not have those 2 settings which mean that you could possible use "any" default mailcow to flood by relaying any other mail instance as you want to flood.
You're also not able to relay a mail from your own mailcow from another "domain" which does not belong to your own mailcow account. You can only relay with your own credentials and your own "domains/accounts".